- If you used what was referred to as a Global IME with a previous version of Office, it will not work with Microsoft Office XP. You will need to download the updated version.
- To download IMEs, you must be a licensed Office user.
- To install East Asian IMEs in Office XP or Office 2003 on Windows 2000, Windows XP or Windows Server 2003, refer to the KB article in the See also box
~ Welcome ~
This words is taken from the "3 idiots" movie which always remembering me to look something fine whatever it was the worst situation ever...
So ?
I want this word "revealed" in our daily activities...
Bring all of problems into happiness and positive thinking... = b
*NB :
I'm not skilled on Grammar, so don't protest me if i have a bad English~ = b
Just give me some comments on my post, but NO HARSH COMMENT okay~=]
For Battle Realms links, I DON'T OWN any links on there. If it's not working, DON'T ASK ME.
This whole blog have been prevent from being "copy-paste", so you CAN'T right click either select the text. -Sorry-
If some link on this blog didn't worked, maybe the upload hosting was closed the link or erase them permanently from their site. *SOPA PIPA* read here
- You can turn off the mp3 player or choose the song on the list as you want -
Recently Listening to Big Bang
Translate to This Languange
Tuesday, 29 March 2011
Free Download East Asian Language
Monday, 28 March 2011
REPOST : Solusi BlueScreen Windows XP
BsoD (Blue Screen of Death)
Pesan Stop ini umumnya terjadi karena kesalahan atau tidak kompatibelnya (tidak cocok) hardware dan software. Bisa juga terjadi karena setting BIOS yang kurang tepat.
- Sebuah aplikasi, seperti program backup, tidak mengalokasikan dengan benar sejumlah besar memori kernel.
Peringatan: jangan melakukan perubahan pada registry kecuali Anda tidak punya pilihan lain karena hal ini mem-bypass keamanan standar yang dapat merusak sistem Anda, bahkan Anda mungkin terpaksa meng-install ulang Windows. Jika Anda benar-benar harus meng-edit registry, backup-lah registry Anda terlebih dahulu.
REPOST : How to remove XP Security Tool 2010, XP Defender Pro, and Vista Security Tool 2010 (Uninstall Guide)
Posted by Grinler on January 27, 2010 @ 10:08 PM
What this infection does:
XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro are all new rogues that are exactly the same program. They are just shown with different names and interfaces depending on the version of Windows that it is run on. This guide run under quite a few different names, which I have listed below based upon the version of Windows:
Windows XP Rogue Name Windows Vista Rogue Name Windows 7 Rogue Name
AntiSpyware XP AntiSpyware Vista AntiSpyware Win 7
AntiSpyware XP 2010 AntiSpyware Vista 2010 AntiSpyware Win 7 2010
Antivirus XP Antivirus Vista Antivirus Win 7
Antivirus XP 2010 Antivirus Vista 2010 Antivirus Win 7 2010
Total XP Security Total Vista Security Total Win 7 Security
XP AntiSpyware 2010 Vista Guardian Win 7 Antispyware 2010
XP Antivirus Pro Vista Security Tool Win 7 Antivirus Pro
XP Guardian Vista Security Tool 2010 Win 7 Guardian
XP Security Tool Vista Smart Security Win 7 Security Tool
XP Security Tool 2010 Vista Smart Security 2010 Win 7 Security Tool 2010
XP Smart Security Vista AntiMalware Win 7 Smart Security
XP Smart Security 2010 Vista AntiMalware 2010 Win 7 Smart Security 2010
XP AntiMalware Vista AntiSpyware Win 7 AntiMalware
XP AntiMalware 2010 Vista AntiSpyware 2010 Win 7 AntiMalware 2010
XP Antivirus Pro Vista Antivirus Pro Win 7 Antivirus Pro
XP Defender Vista Defender Win 7 Defender
XP Defender Pro Vista Defender Pro Win 7 Defender Pro
XP Security Vista Security Win 7 Security
XP Security 2010 Vista Security 2010 Win 7 Security 2010
XP Internet Security Vista Internet Security Win 7 Internet Security
XP Internet Security 2010 Vista Internet Security 2010 Win 7 Internet Security 2010
When installed, this rogue pretends to be an update for Windows installed via Automatic Updates. It will then install itself as a single executable called AV.exe that uses very aggressive techniques to make it so that you cannot remove it. First, it makes it so that if you launch any executable it instead launches XP Security Tool 2010, XP Defender Pro, or Vista
Defender Pro. If the original program that you wanted to launch is deemed safe by the rogue, it will then launch it as well. This allows the rogue to determine what executables it wants to allow you to run in order to protect itself. It will also modify certain keys so that when you launch FireFox or Internet Explorer it will launch the rogue instead and display a fake firewall warning. Last, but not least, when try to browse to a web site, it will hijack your browser and state that the site is a security risk and not allow you to visit it.

Vista Antispyware 2010
For more screen shots of this infection click on the image above.
There are a total of 14 images you can view.
Once started, the rogue itself, like all other rogues, will scan your computer and state that there are numerous infections on it. If you attempt to use the program to remove any of these infections, though, it will state that you need to purchase the program first. In reality, though, the infections that the rogues states are on your computer are all legitimate files that if deleted could cause Windows to not operate correctly. Therefore, please do not trust anything it states are infections.
While running, XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro will also display fake security alerts on the infected computer. The text of some of these alerts are:
Tracking software found!
Your PC activity is being monitored. Possible spyware infection. Your data security may be compromised. Sensitive data can be stolen. Prevent damage now by completing security scan.
XP Internet Security 2010 Firewall Alert!
XP Internet Security 2010 has blocked a program from accessing the Internet
Internet Explorer is infected with Trojan-BNK.Win32-Keylogger.gen
Private data can be stolen by third parties, including credit card details and passwords.
Just like the scan results, these fake security warnings and alerts are all fake and should be ignored.
Without a doubt, this rogue is designed to scam you out of your money by hijacking your computer and trying to trick you into thinking you are infected. Therefore, please do not purchase this program , and if you have, please contact your credit card company and dispute the charges. Finally, to remove XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro please use the guide below, which only contains programs that are free to use.
Threat Classification:
Advanced information:
View XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro files.
View XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro Registry Information.
Tools Needed for this fix:
Guide Updates:
01/27/10 - Initial guide creation.
01/27/10 - Updated for new rogue names.
01/28/10 - Updated for new rogue names.
02/03/10 - Updated for new rogue names.
03/17/10 - Updated for new version of rogue and new names.
03/22/10 - Updated removal instructions
Automated Removal Instructions for XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro using Malwarebytes' Anti-Malware:
- For the first part of this removal guide you will need to use a different computer than the infected one. This is also a tricky rogue to remove, so please follow the instructions carefully. If you are concerned about whether or not you can do this, do not be, as I have made these instructions easy to follow for people of any computer expertise.
- From another computer, please download Malwarebytes' Anti-Malware, or MBAM, and the reg files from the following locations and save it to an external media such as an external hard drive or a USB flash
drive
. We will then use the external drive or flash drive to to transfer these files to your infected computer. If you do not own a USB flash drive, you can get one from any local or online computer store for a small price. Some examples of good and cheap ones can be found at Newegg and Best Buy. The files that you should download onto this device are:
Malwarebytes' Anti-Malware Download Link (Download page will open in a new window) - Everyone should download this
FixExe.reg - Everyone should download this
- Once you have downloaded all the necessary files to a removable device, you need to plug it into your infected computer so it can access them.
- On the infected computer make sure XP Internet Security 2010, Antivirus Vista 2010, or Win 7 Antispyware 2010 is running. If it is not, you can launch it by running any program on your computer as that will trigger the rogue program to run. Once running, do not close it during the entire length of this guide.
- Now open the drive that corresponds to the removable media that you copied the programs from step 2 onto. Once open, double-click on the FixExe.reg file. When Windows prompts whether or not you want to allow the data to be added to your computer, click on the Yes button.
- Now you should be able to run the mbam-setup.exe file that you saved on your removable media in step 2. Double-click on this file to install MalwareBytes' on to your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure you leave both the Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware checked. Then click on the Finish button. If you already have MalwareBytes' installed, simply launch it now and continue to step 8.
- MBAM will now automatically start and you will see a message stating that you should update the program before performing a scan. As MBAM will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main program as shown below.

- On the Scanner tab, make sure the the Perform full scan option is selected and then click on the Scan button to start scanning your computer for XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro related files.
- MBAM will now start scanning your computer for malware. This process can take quite a while, so we suggest you go and do something else and periodically check on the status of the scan. When MBAM is scanning it will look like the image below.

- When the scan is finished a message box will appear as shown in the image below.

You should click on the OK button to close the message box and continue with the XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro removal process.
- You will now be back at the main Scanner screen. At this point you should click on the Show Results button.
- A screen displaying all the malware that the program found will be shown as seen in the image below. Please note that the infections found may be different than what is shown in the image.

You should now click on the Remove Selected button to remove all the listed malware. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. When removing the files, MBAM may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot, please allow it to do so. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps.
- When MBAM has finished removing the malware, it will open the scan log and display it in Notepad. Review the log as desired, and then close the Notepad window.
- You can now exit the MBAM program.
- As many rogues and other malware are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here:
How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector
Your computer should now be free of the XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro programs. If your current anti-virus solution let this infection through, you may want to consider purchasing the PRO version of Malwarebytes' Anti-Malware to protect against these types of threats in the future.
If you are still having problems with your computer after completing these instructions, then please follow the steps outlined in the topic linked below:
Preparation Guide For Use Before Using Malware Removal Tools and Requesting Help
Associated XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro Files:
Windows XP:
c:\Documents and Settings\All Users\Application Data\QJyrk5wvCU1
%UserProfile%\Local Settings\Application Data\av.exe
%UserProfile%\Local Settings\Application Data\ave.exe
%UserProfile%\Local Settings\Application Data\QJyrk5wvCU1
%UserProfile%\Local Settings\Application Data\WRblt8464P
%UserProfile%\Local Settings\Temp\QJyrk5wvCU1
%UserProfile%\Templates\QJyrk5wvCU1
Windows Vista and Windows 7:
C:\ProgramData\QJyrk5wvCU1
C:\Users\All Users\QJyrk5wvCU1
%UserProfile%\AppData\Local\av.exe
%UserProfile%\AppData\Local\ave.exe
%UserProfile%\AppData\Local\QJyrk5wvCU1
%UserProfile%\AppData\Local\WRblt8464P
%UserProfile%\AppData\Local\Temp\QJyrk5wvCU1
%UserProfile%\AppData\Roaming\Microsoft\Windows\Templates\QJyrk5wvCU1 File Location Notes:
%UserProfile% refers to the current user's profile folder. By default, this is C:\Documents and Settings\ for Windows 2000/XP, C:\Users\ for Windows Vista/7, and c:\winnt\profiles\ for Windows NT.
Associated XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro Windows Registry Information:
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "AntiVirusOverride" = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "FirewallOverride" = "1"
Source : http://www.bleepingcomputer.com/virus-removal/remove-antivirus-vista-2010
Vista Antispyware 2010
For more screen shots of this infection click on the image above.
There are a total of 14 images you can view.
Your PC activity is being monitored. Possible spyware infection. Your data security may be compromised. Sensitive data can be stolen. Prevent damage now by completing security scan.
XP Internet Security 2010 Firewall Alert!
XP Internet Security 2010 has blocked a program from accessing the Internet
Internet Explorer is infected with Trojan-BNK.Win32-Keylogger.gen
Private data can be stolen by third parties, including credit card details and passwords.
View XP Security Tool 2010, XP Defender Pro, Vista Security Tool 2010, and Vista Defender Pro Registry Information.
01/27/10 - Updated for new rogue names.
01/28/10 - Updated for new rogue names.
02/03/10 - Updated for new rogue names.
03/17/10 - Updated for new version of rogue and new names.
03/22/10 - Updated removal instructions
Malwarebytes' Anti-Malware Download Link (Download page will open in a new window) - Everyone should download this
FixExe.reg - Everyone should download this
You should now click on the Remove Selected button to remove all the listed malware. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. When removing the files, MBAM may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot, please allow it to do so. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps.
How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector
c:\Documents and Settings\All Users\Application Data\QJyrk5wvCU1
%UserProfile%\Local Settings\Application Data\av.exe
%UserProfile%\Local Settings\Application Data\ave.exe
%UserProfile%\Local Settings\Application Data\QJyrk5wvCU1
%UserProfile%\Local Settings\Application Data\WRblt8464P
%UserProfile%\Local Settings\Temp\QJyrk5wvCU1
%UserProfile%\Templates\QJyrk5wvCU1
Windows Vista and Windows 7:
C:\ProgramData\QJyrk5wvCU1
C:\Users\All Users\QJyrk5wvCU1
%UserProfile%\AppData\Local\av.exe
%UserProfile%\AppData\Local\ave.exe
%UserProfile%\AppData\Local\QJyrk5wvCU1
%UserProfile%\AppData\Local\WRblt8464P
%UserProfile%\AppData\Local\Temp\QJyrk5wvCU1
%UserProfile%\AppData\Roaming\Microsoft\Windows\Templates\QJyrk5wvCU1 File Location Notes:
%UserProfile% refers to the current user's profile folder. By default, this is C:\Documents and Settings\ for Windows 2000/XP, C:\Users\ for Windows Vista/7, and c:\winnt\profiles\ for Windows NT.
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\av.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_CLASSES_ROOT\secfile\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = "%UserProfile%\Local Settings\Application Data\ave.exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "AntiVirusOverride" = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "FirewallOverride" = "1"
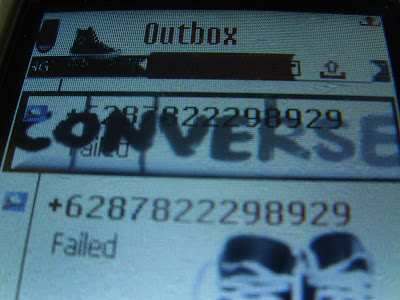
Your NOKIA send MMS by itself ? (MMS terkirim sendiri ?)
5. Install antivirus in your HP with : http://rapidshare.com/#!download|305dt|118200207|All_Mobile_Antivirus.rar|8851